VPNs can seem like a complicated technology, packed with low-level geeky details that hardly anyone understands, but check the TunnelBear site and you'll quickly realize this service does things differently.
The Canadian-based, McAfee-owned company doesn't drown you in jargon. There's little talk of protocols, no mention of encryption types, barely any technical terms at all. Instead the site focuses on the fundamentals, such as clearly explaining why you might want to use a VPN in the first place.
This approach won't work for everyone. If you're an experienced user and want to get down to the technical details of the service, for instance, you're likely to be disappointed. For example, the Support site returns one article if you search for DNS, one for OpenVPN, and nothing at all for MTU. The content you do get is clear and straightforward, but it can't compete with providers like ExpressVPN, where a search for DNS alone gets you almost 60 in-depth hits.
- Want to try TunnelBear? Check out the website here
The service has a relatively small network, with locations in 23 countries only covering North America, Europe, Brazil, Mexico, Japan, India, Singapore, Hong Kong, Australia and New Zealand. TunnelBear dropped its Hong Kong location after China imposed its new security laws, but has added Argentina to the list.
This is plainly a long way behind NordVPN's 59 countries and ExpressVPN's 94, but all that really matters is the locations you need. If they're all on TunnelBear's list, you shouldn't have any issues.
Setup is easy on all the main platforms, thanks to custom clients for iOS, Android, Mac and Windows, as well as extensions for Chrome, Firefox and Opera. But again, there's not a lot for demanding users, with no help for getting the service working on routers, games consoles, Chromebooks, Linux, with OpenVPN, or anything else.
Still, if you're happy with the regular apps, TunnelBear's support for up to five simultaneous connections means you'll be able to have most of your devices running at the same time.
TunnelBear's free account provides a horribly limited 500MB of traffic a month, barely enough to run even a single simple speed test.
Its monthly plan gives you unlimited data for a reasonable $9.99 a month, though. The price drops to an effective $4.99 a month on the annual plan, or $3.33 if you sign up for three years.
The three-year plan also comes with full use of the RememBear Password Manager at no extra cost. That's normally priced at $2.50 a month on its longest two-year plan.
If you'll use RememBear, that's a great deal, but if you only need the VPN, there are cheaper providers around. Surfshark's two-year plan is a monthly $2.49, and Ivacy has a five-year plan for $1.16 a month. (Okay, we don't like long-term contracts either, but look at the totals: one year of TunnelBear costs $59.88, five years of Ivacy is just $69.99.)
If you do sign up for TunnelBear, keep in mind that there's no money-back guarantee. The small print says: "While all amounts paid are non-refundable, certain refund requests for subscriptions may be considered by TunnelBear on a case-by-case basis." Presumably, you might get a refund if you've had really bad service, but it's entirely up to the company to decide what should happen. Not quite as friendly as the cuddly cartoon bears suggest, then.
There's a small plus in TunnelBear's Bitcoin support. This is limited, though – it's available with the one-year plan only, not the monthly or three-year options – and elsewhere, there's no PayPal support; it's strictly card-only.
Privacy and logging
TunnelBear's privacy policy is one of the most thorough we've seen from any VPN provider, with in-depth information on everything the service collects, and everything it doesn't. We do mean thorough, too – the details go right down to the names, purposes and expiry dates of the cookies used by TunnelBear.com.
The logging policy is clearly described, with TunnelBear explaining that it does not collect "IP addresses visiting our website", "IP addresses upon service connection", "DNS Queries while connected", or "Any information about the applications, services or websites our users use while connected to our Service." As a result, the company says, it can't link any of its users to an action carried out by a specific IP address. Sounds good to us.
The service does record what it calls 'operational data', updating this when you connect to the network. That includes the OS version of your device, TunnelBear app version, whether you've been active this month and the bandwidth you've used. Not quite zero logging, then, but it's far less than we've seen elsewhere, and there's nothing here that anyone could use to begin to link you to a specific online action.
While that looks great, there's normally no way to tell whether you should trust what a VPN provider is telling you. But TunnelBear is a little different. The company now has independent specialists Cure53 run an annual public security audit covering many different areas of the service. (The third audit, covering 2019, included the mobile and Windows clients, browser extensions, the service infrastructure, backend and frontend systems, and the public website.)
The audit results weren't perfect (we would have been suspicious if they were), and the report detailed several vulnerabilities, with two of them critical. That's no surprise when a service puts itself under this level of scrutiny, though, and all issues are now fixed.
Overall, we must applaud TunnelBear for its level of transparency, which tramples all over most of the competition. Most VPNs have never had any form of security audit, and the providers who have actually made some movement in this direction, typically have one-off audits with a far narrower scope. That's just not good enough, and it's great to see TunnelBear leading the way.
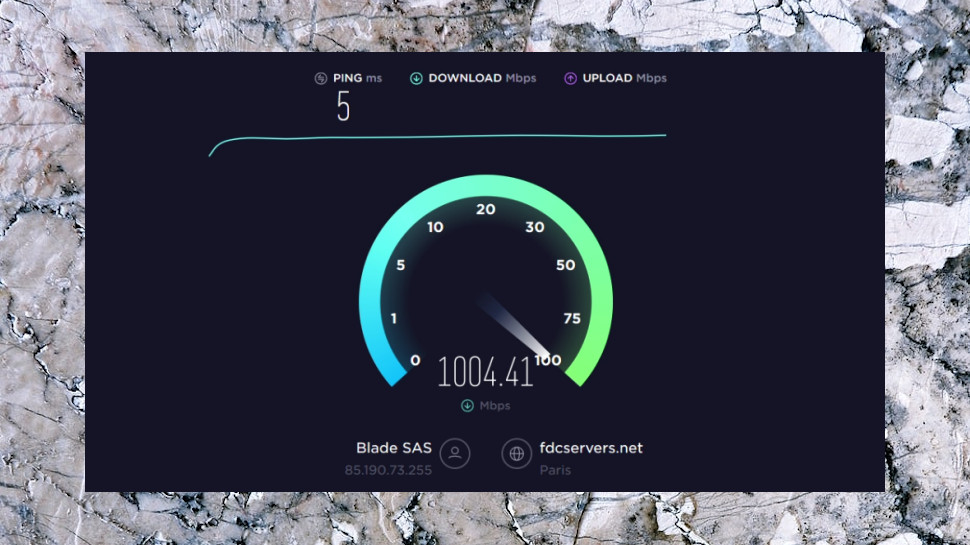
Performance
To check out TunnelBear's performance, we first logged on to each server, recorded the connection time, ran a ping test to look for latency issues and used a geolocation check to verify that the server was indeed in the advertised country.
We ran this test twice, 12 hours apart, and managed to connect to each server without difficulty, no retries required. Connection times were mid-range at 4-6 seconds. The ping times were variable, but not enough to show any significant issue.
Next, we used benchmarking websites TestMy.net and Ookla's SpeedTest to check TunnelBear's download speeds from a UK data center and a US location with a 600Mbps line.
UK downloads were variable but above average at 140-230Mbps. That's better than Surfshark's most recent results (70-150Mbs) and comparable with IPVanish (150-210Mbps), but can't match the consistency of Hotspot Shield (190-210Mbps) or the pace of NordVPN (310-390Mbps.)
US speeds averaged a similar 160Mbps, a little below the 200Mbps we saw in the last review, but still a solid result which competes well with many big names.
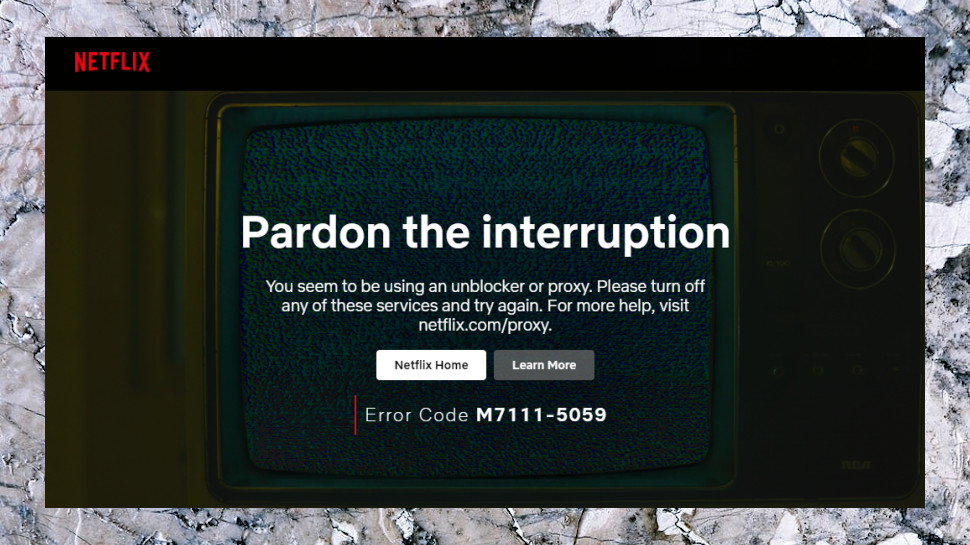
Netflix
One of the major selling points of a VPN is that it can make you appear to be visiting a website from another country, perhaps giving you access to content you wouldn't be able to view otherwise. But this doesn't always work, so we test all VPNs with Netflix and more to see if they can give us access to various streaming sites.
We logged into TunnelBear's UK location and tried accessing BBC iPlayer, but the site noticed our VPN-based trickery and warned 'this content is not available in your location.'
There was more success with US-only YouTube channels, where we streamed videos without difficulty. That's a plus point, but not a major one, as just about every VPN with a US location can do the same.
US Netflix is generally much more of an unblocking challenge, and this time it seemed too much for TunnelBear. Whatever we tried (including connecting to the UK and France), Netflix displayed its standard 'you seem to be using an unblocker or proxy' error message and refused to stream content.
There was no luck with Amazon Prime Video, either. Forget accessing US content, we couldn't even stream UK movies using our UK account.
Our unblocking tests at least ended on a high note, though, as TunnelBear allowed us to access US Disney+. That's great news (and an improvement on the last review), but it can't make up for the earlier unblocking performance. If you're hoping to access geoblocked content, check out your target sites with the free TunnelBear plan before you part with any cash.
Torrents
VPNs usually don't like to shout about their torrent support, and it's not difficult to see why. Torrent users are likely to gobble up much more bandwidth than others, and if that involves downloading illegal stuff, it could generate more attention from the copyright police.
TunnelBear takes this quiet approach to an extreme, though, with barely any references to P2P and torrents on the entire TunnelBear website.
Undaunted, we raised a query with the support team, and a polite response soon arrived. TunnelBear supports torrents at all locations, the agent explained, but they also recommended specific tunnels (Canada, US, UK, Romania, Netherlands, Germany, Sweden) if we had problems elsewhere.

Client setup
Getting started with TunnelBear begins by handing over your email address to create an account. Accept the free option or hand over your cash for one of the paid plans, and you're offered a choice of apps for Windows, Mac, iOS and Android, as well as browser extensions for Chrome, Firefox and Opera.
If you're looking for anything more advanced, you're going to be disappointed. There's nothing for routers, or games consoles, or smart TVs, or anything else. There are no links to installation guides or troubleshooting advice. Bizarrely, the page doesn't even link to TunnelBear's OpenVPN configuration files, to help you set up other devices manually. These are available, but you have to look very hard to find them (we tracked them down in a blog post about Linux support.)
If you're happy with TunnelBear's main apps, you're unlikely to notice any issues (if anything, the focus on the major platforms makes the website easier to navigate). But given that TunnelBear does have useful setup information regarding Linux, OpenVPN and more, we think the website should make this more accessible to its users.
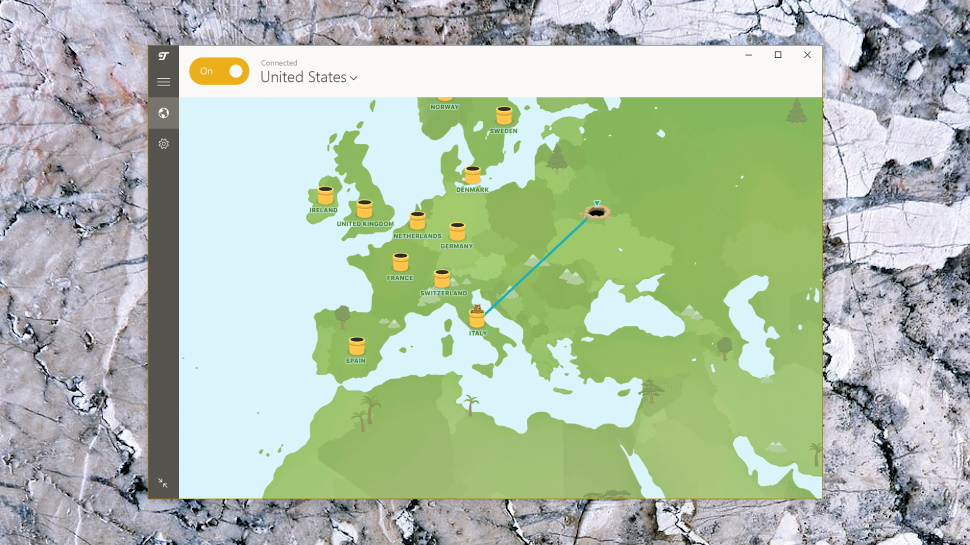
Windows client
TunnelBear's Windows VPN client opens with a grey world map, centered on your current location, with all the other VPN locations highlighted.
Map interfaces can look good, but they're not very practical to use, and this one is no exception. There's no zoom option to help you get an overview, for instance, and although you can click and drag to move your viewpoint, this won't wrap around. Scroll in any direction, you'll soon bump into the map edge and have to scroll back.
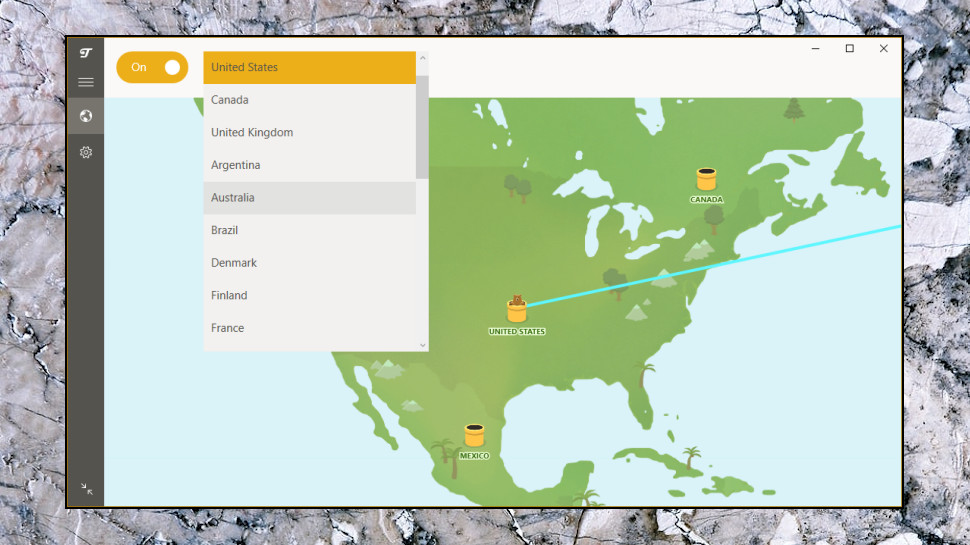
You can also select your location in a more conventional way, by clicking the current destination at the top of the screen and choosing something else from a drop-down list. That's simple, but very plain; it's just a simple text list, with no indications of server load, ping time or anything else.
Once you've chosen a location, clicking On gets you connected, and the client displays a 'connection' animation, panning the screen and plotting a line across the map to your destination. This looks good, but the client goes into overload if you choose one server while connected to another, as it pointlessly scrolls and displays animations at all three locations (previous, physical and the new location.)
Connection times were reasonable for us at 2-10 seconds, depending on the distance to the server. The client displayed native Windows desktop notifications to tell you when it connected or disconnected, handy as you're able to tell when your connection is protected, even if the Windows client is minimized or covered by another application window.
The client's protocol handling is a little, well, unusual. It supports OpenVPN primarily, with IKEv2 as a secondary option, but you don't get to choose; the client decides, based on who-knows-what rules, and the interface doesn't tell you what that decision was. So, although there's an option to use OpenVPN TCP rather than UDP connections, if the client is using IKEv2, it'll have no effect at all.
The client doesn't have many settings, but the few you get are very useful. You can have it load when Windows starts, for instance, then automatically activate the VPN whenever you access a wireless network which isn't on a custom Trusted Network list (everywhere but home and work, say).
The Obfsproxy-based GhostBear attempts to make your activities look more like regular internet traffic, perhaps helping you connect in countries like China which try to detect and block use of VPNs.
A VigilantBear setting is essentially a kill switch, blocking all internet traffic if the VPN drops to prevent any identity leaks. We've tested this in the past by forcibly closing an OpenVPN connection and it performed well, detecting the problem, blocking internet access, warning us with a desktop notification and reconnecting within seconds.
Unfortunately, this time the client connected via IKEv2 (don't ask us why), and the results were very different. When we closed our IKEv2 connection, internet traffic continued to flow, now entirely unprotected. Our exposure was limited - the client still warned us of the problem and restored the connection within seconds - so reducing any risks, but this is still a clear failure. And the inability to choose your protocol or easily see what the client is using, makes this even worse, as you'll never know whether you're connected via safe OpenVPN or vulnerable IKEv2.
Overall, TunnelBear's Windows client is easy to use, but there's clearly lots of scope for improvement, particularly with the kill switch, and the basic feature list could disappoint experienced users.
Mobile apps
TunnelBear's Android and iOS apps have a very similar look and feel to the Windows edition. There's a world map with VPN locations highlighted, a list of locations as a simpler alternative, a small number of useful settings, and not much else.
The map works a little better than the desktop version. It wraps as you expect, for instance (you can keep swiping left or right and get back to where you started). There's still no zoom, but the Android app can at least switch from portrait to landscape to give you a better view.
Server selection looks much the same, as you're able to choose locations from the map or the location list. Connections take a similar 2-10 second time as on the desktop, but with less of the pointless scrolling and map animations that we saw on the desktop.
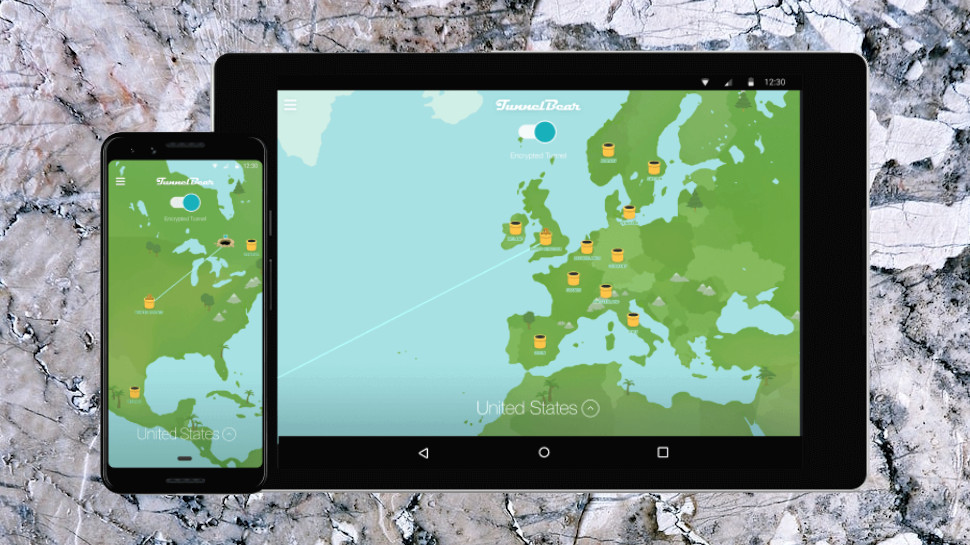
Settings deliver most of the benefits of the desktop client, like auto-connect whenever you're not accessing a trusted network, the VigilantBear kill switch, and GhostBear to try and avoid VPN blocking.
There's a welcome bonus in SplitBear (aka split tunneling), where you can choose apps which will always use your regular connection, rather than be routed via TunnelBear. You may never use this feature, but if you find the VPN breaks a particular app, you'll be glad it's there.
The 'display fluffy clouds on the map' setting seems to have disappeared since our last review, and although it was probably the least essential VPN feature we've ever seen, that still leaves us feeling a little sad. Still, the option to enable or disable Bear Sounds is there, so it's not all bad news.
TunnelBear’s iOS app has a similar look and feel to its Android cousin, though unfortunately with the same annoying connection animations as the desktop builds.
It drops most of the more advanced features from the other platforms. You can forget SplitBear's split tunneling, GhostBear-type obfuscation or the VigilantBear kill switch. There's a valuable extra in the ability to connect automatically for untrusted networks, though, along with somewhat less important options to enable or disable Bear Sounds, and choose a custom app icon.
Put it all together and our verdict on the mobile VPN apps is much the same as the desktop client. They get the job done and they're fine for simple use, but there are plenty of better and more feature-rich VPN apps around.
Browser extensions
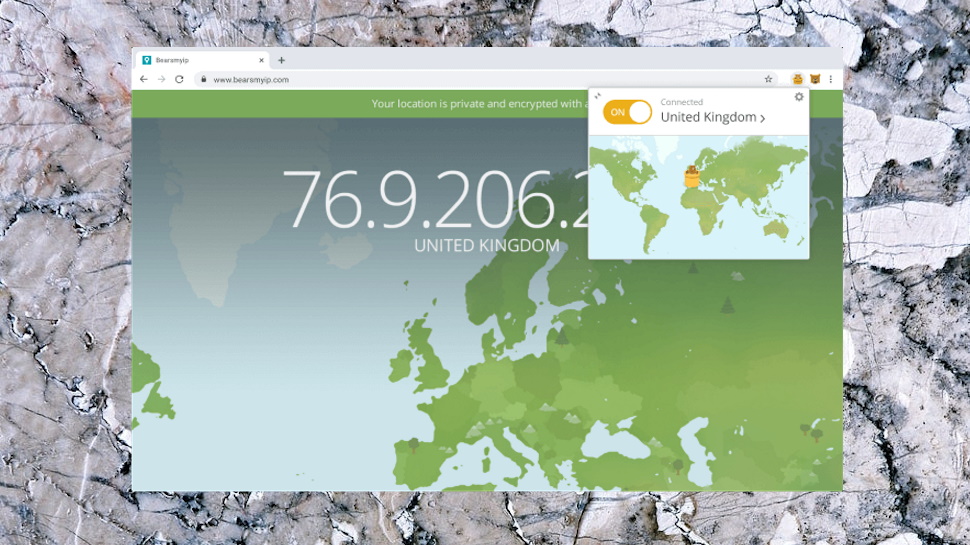
Installing TunnelBear's browser extensions can make the service easier to operate, by allowing you to choose a location, connect and disconnect from inside your browser. The extensions work as proxies and so only protect your browser traffic, but if that's all you need, the extra convenience could make them worth a try.
The Chrome extension added an icon to our address bar, and tapping this enabled choosing new locations from a drop-down list.
Hit the Connect button and, as usual with proxies, you're connected instantly. A tiny map updates to show your location, similar to the regular apps.
There are no extra features, no WebRTC or tracker blocking or anything else. But the extension does have a small usability plus in its keyboard shortcut support. If you want to keep your hands off the mouse, pressing Ctrl+Shift+U will connect you to the VPN, and pressing it again will toggle the connection off when you're done. (A separate Alt+Shift+N shortcut toggles the connection on and off in Incognito mode.)
We checked the Firefox extension to see if it had any more options, but no, it looked and worked much the same as the Chrome version.
The browser extensions follow a very similar pattern to the apps, then – they are short on features, but relatively simple, and fine for the target audience of casual users.
Support
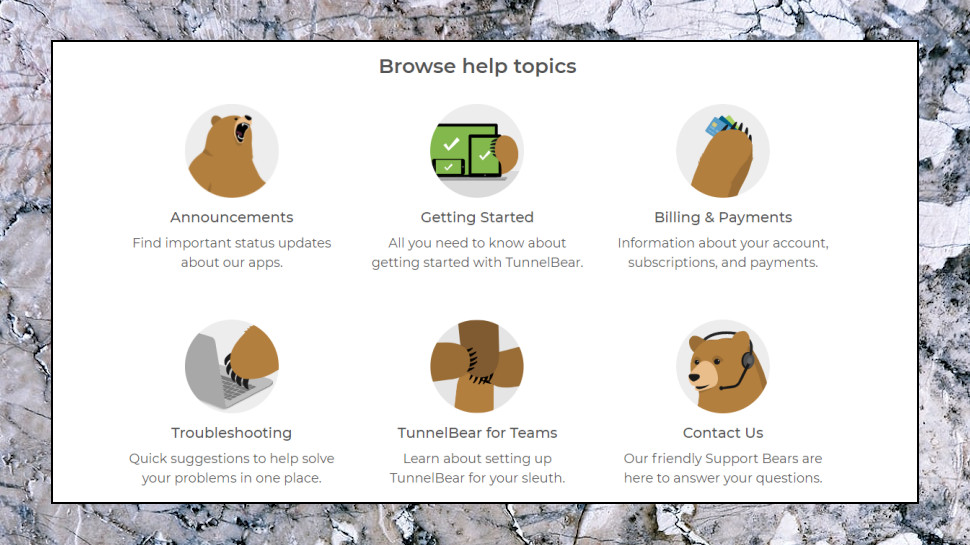
TunnelBear support starts with its web-based help site. This is presented in a clear and simple way, with large icons pointing you to key areas (Getting Started, Troubleshooting, Billing), and basic articles on the most common questions ('Why should I trust TunnelBear?', 'Why can't I access the content I want?', 'Does TunnelBear keep logs?').
Go searching for answers and you'll find TunnelBear's knowledgebase doesn't have a lot of content, but what you get is well presented and gives you a decent range of information. The Connection Issues page doesn't just offer generic 'reinstall'-type ideas, for instance. It links you to TunnelBear's Twitter page to look for service information, suggests trying out the service on another network, and points you to settings which might help.
Despite its beginner-oriented approach, there's also room for just a few more advanced tweaking ideas, with recommendations for ports which should be opened in some circumstances.
There's no live chat support, but if you need more in-depth help, a Contact page allows you to send a message to the support team. This prompts you for the type of problem, affected locations, operating system and so on, a smart way to ensure beginners provide all the key information.
We kept our test question simple, and had a friendly, helpful and accurate reply in three and a half hours. We would still prefer the near-instant response of quality live chat – because if your problem is complex and requires a lot of back and forth, questions and answers, it could take a very long time to find a solution – but as email support goes, TunnelBear isn't bad at all.
Final verdict
It's not the largest, fastest or most powerful of VPNs, but TunnelBear's ease of use and strong focus on opening up its systems to scrutiny deserve a lot of credit. We hope it fixes the Windows kill switch soon, but otherwise TunnelBear is worth a look, particularly for newbies.
- Also check out the best VPN services of 2020
from TechRadar - All the latest technology news https://ift.tt/2FpW6iC
via IFTTT
0 التعليقات: